Customer Benefits

Solution Background
As the business expands, the exposure of enterprises in the external environment continues to increase. Whether it is the enterprise's website facing the Internet, cloud service applications, or the network connections with partners and third-party suppliers, all these constitute a complex and vast external attack surface. Globally, incidents where enterprises suffer external attacks resulting in data leaks, business disruptions, etc., occur frequently, causing huge economic losses, reputational damage, and legal liability risks to enterprises. Under such a severe cybersecurity situation, the traditional security protection model has been unable to meet the needs of enterprises to defend against external attacks. The external attack surface management service has emerged, which through comprehensive and continuous monitoring and management of the enterprise's external attack surface, helps enterprises promptly discover and fix potential security vulnerabilities, effectively reducing the risk of being attacked by the outside world, and becoming a key measure for enterprises to ensure information security and achieve sustainable development.
Requirement Analysis
Solution Introduction
External attack surface management solutions help enterprises continuously identify, monitor, and manage their externally visible digital assets. By detecting internet-exposed systems, shadow IT, and misconfigurations, these tools aim to promptly identify and mitigate potential risks before they can be exploited by attackers. Services include:
- Shadow IT Discovery : Detect unknown or unauthorized SaaS applications, illegal domains, and untracked cloud instances.
- Third-party risk management : Assess the external attack surface risk of suppliers, partners, or outsourcers.
- Cloud security monitoring : Identify cloud resource misconfigurations, public storage buckets, and exposed APIs.
- Incident prevention : Proactively detect potential attack paths to reduce the possibility of data leakage or ransomware attacks.
- Compliance support : Ensure asset visualization and risk remediation meet regulatory requirements (such as ISO/IEC 27001, Level 1 Protection Level, etc.).
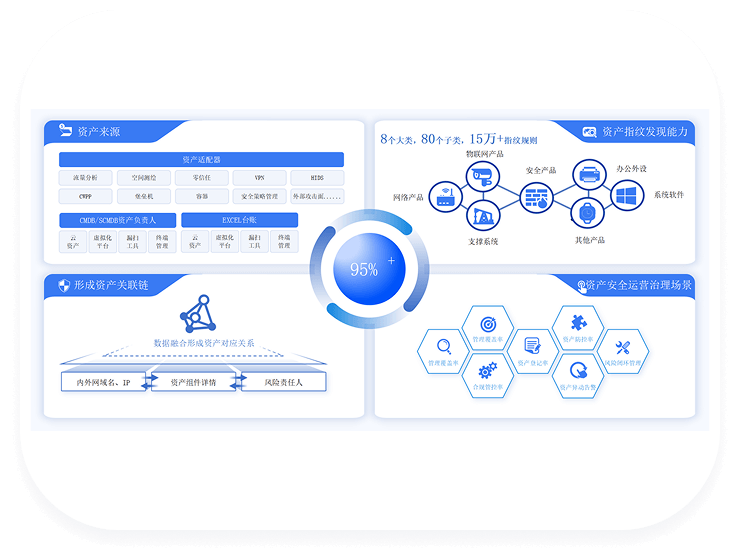
Solution Advantages

Advanced technology integration
Through the collaborative work between various technical tools, the accuracy of attack surface analysis, the depth of vulnerability detection and the scientific nature of risk assessment have been greatly improved, providing enterprises with comprehensive and accurate security management support.

Comprehensive service coverage
The service covers the entire process of external attack surface management, from attack surface analysis, vulnerability detection, risk assessment to vulnerability remediation management and continuous monitoring and early warning, providing enterprises with a one-stop solution.

Automation and intelligence
The extensive use of automation technologies and intelligent analysis algorithms has enabled automated attack surface discovery, intelligent vulnerability detection, and automated management of vulnerability remediation processes, significantly improving management efficiency and reducing human error.

Third-party collaborative management
A comprehensive third-party security assessment and collaborative management mechanism has been established to effectively help enterprises manage and control security-related risks with third-party suppliers.






