Customer Benefits
Solution Background
As enterprise digital transformation accelerates, business architectures are growing more complex. The adoption of cloud computing, IoT, and mobile workforces has blurred network boundaries, drastically increasing security management challenges. Facing high costs, talent shortages, and slow technology updates, many organizations struggle to build and maintain effective in-house security operations. Managed security services have emerged as a practical solution, offering comprehensive, professional, and continuous protection to help enterprises operate confidently in today’s dynamic cyber environment.
Requirement Analysis
Solution Introduction
By integrating cybersecurity capabilities such as threat intelligence, security automation, incident response, and threat detection, we enable rapid full-lifecycle operational management through close team collaboration. Based on standard frameworks and industry best practices, we help enterprises quickly understand security trends and threat landscapes, providing uninterrupted information security assurance.
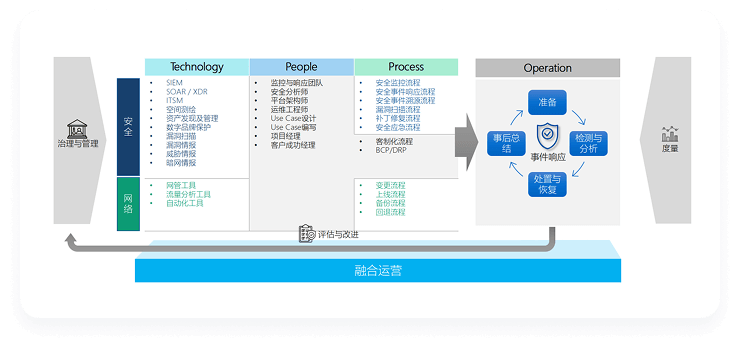
Solution Advantages

Comprehensive security operations coverage
The service covers all aspects of security operations, from data collection and analysis, threat detection and response to security management and compliance assurance, providing enterprises with one-stop security solutions.

Continuous security and optimization
The service team continuously optimizes security operation strategies and processes based on changes in the network security situation and the development of corporate business, continuously improves the company's security protection capabilities, and ensures that the company always maintains a high level of security.

Professional team and authoritative certification
The security team brings together many top security experts in the industry, who are able to accurately respond to various complex network security challenges and provide enterprises with high-quality and reliable security operation services.

Customized service solutions
We gain an in-depth understanding of the company's unique business model, network architecture, and security needs to ensure that the service plan is closely aligned with the company's actual situation, maximize the benefits of the service, and meet the company's security operation needs at different stages of development.






