Customer Benefits

Solution Background
In today's rapidly developing digital age, business operations are highly dependent on information technology systems and network environments. If an information security incident occurs, without an effective emergency response mechanism, the company could suffer significant economic losses, legal liability, and irreparable reputational damage. Therefore, security emergency response services are crucial for companies to quickly restore order, mitigate losses, and maintain stability and development in times of crisis.
Requirement Analysis
Solution Introduction
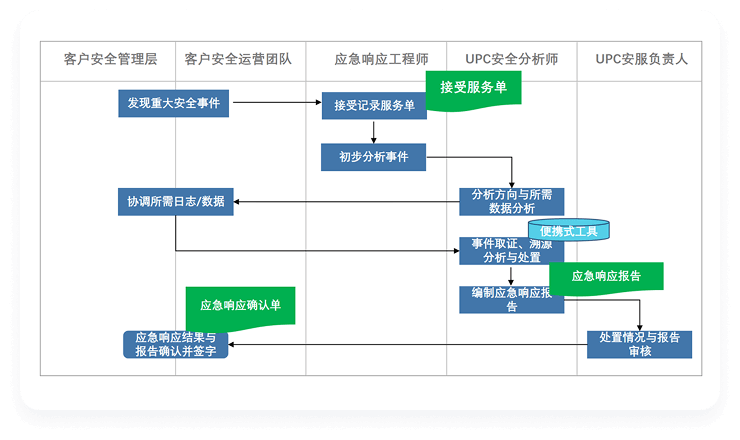
In the event of major security incidents (ransomware attacks, data theft, vulnerability attacks, compromised hosts, etc.), we offer services for incident location and evidence collection, isolation and removal, digital forensic analysis, and security reinforcement. The service content includes:
- Evidence collection and location: Identify the source of the threat and conduct forensic analysis. Utilize intelligence data to uncover more compromised nodes within the system.
- Isolation and Clearance : Analysts use professional tools to conduct comprehensive and in-depth isolation and clearance of files, registry keys, scheduled tasks, startup items, etc.
- Forensic analysis: Comprehensive attack attribution and forensic analysis is conducted through behavioral and sample examination, covering compromised systems, attack vectors, and threat actor profiling, to further unveil the complete picture of the incident.
- Hunting prediction : Relying on hacker tracking and tracing and hunting technology, we continuously track the attackers of threat events, discover changes in the attackers' assets and technologies, and guide enterprises to take early prevention measures.
- Security reinforcement suggestions: Provide reinforcement recommendations for vulnerability weak points, security systems, and response procedure.
- Emergency Response Report : Describes and analyzes the incident emergency response process, and provides professional advice on disposal strategies, security reinforcement, and rectification.
Solution Advantages

Quick response and efficient processing
A comprehensive 24x7 monitoring and emergency response mechanism has been established, which enables rapid intervention in security incidents as soon as they occur, greatly shortening response time.

Advanced technical tools and analytical capabilities
Equipped with a series of advanced security data collection, analysis and evidence collection tools, it can quickly locate problems and provide a solid basis for formulating effective response strategies.

All-round coordination and communication mechanism
We focus on collaboration with all departments within the enterprise and have established a dedicated coordination and communication mechanism to achieve effective integration and efficient utilization of internal resources, enabling the enterprise to form a unified response force when facing security incidents.

Customized service solutions
We tailor emergency response service solutions to each enterprise based on their industry characteristics, network architecture, and business needs, helping them continuously improve their security emergency response mechanisms and overall security protection systems.






