Customer Benefits
Solution Background
In today's increasingly challenging cybersecurity landscape, phishing emails have become a common method used by cyber attackers to breach corporate defenses. Through carefully crafted phishing emails, attackers disguise themselves as legitimate senders, tricking employees into clicking malicious links, downloading malicious attachments, or leaking sensitive information. This allows them to gain access to the company's internal network, posing a serious threat to the company's information assets and business operations. To effectively address this risk, companies urgently need a solution that enhances employee awareness and skills in preventing phishing emails. This solution, designed to simulate real-world phishing attack scenarios, helps companies identify and address weaknesses in phishing prevention, thereby strengthening their overall information security capabilities.
Requirement Analysis
Solution Introduction
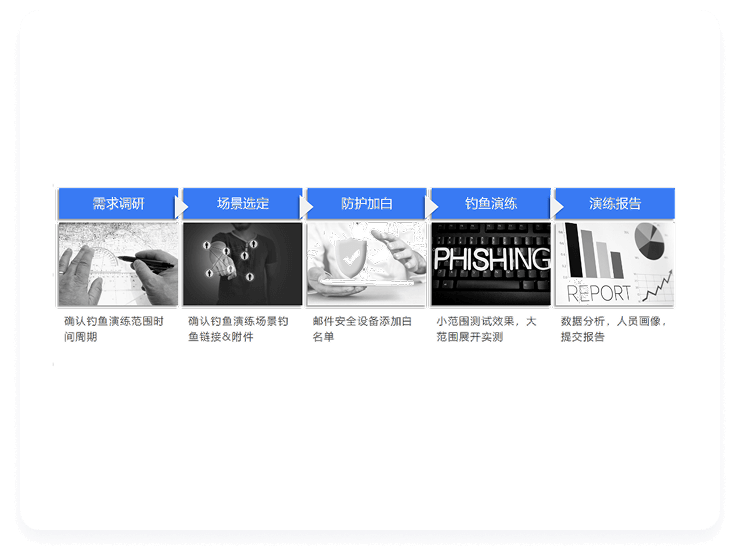
Phishing drill design
- Scenario customization: Design personalized phishing email scenarios based on industry characteristics and corporate business
- Multi-channel drills: Supports phishing attack simulations in various forms, including email, SMS, and instant messaging.
- Target Grouping: Based on the organizational structure, select specific groups of employees to participate in the exercise.
- Phishing email sending: Through the control platform, phishing emails or other attack content are sent regularly.
- Behavior monitoring: Real-time monitoring of user behavior, such as whether they open emails, click links, submit sensitive information, etc.
- Behavioral data statistics: Statistics on the response behaviors of participants (such as open rate, click rate, and leakage rate).
- Risk analysis: Analyze high-risk users or departments and assess potential threats.
Solution Advantages

Personalized plan customization
Design phishing email content and drill scenarios in a targeted manner to make the drill more relevant to the company's actual situation and improve the drill's pertinence and effectiveness.

Precise scene design
From the appearance design of the email to the content writing, from the disguise of the sender information to the setting of malicious links and attachments, everything is done to simulate real phishing attack techniques as much as possible.

Real-time monitoring and analysis
By using a professional drill platform to monitor employees' email operations in real time and collect data, we can understand employees' reactions and prevention situations in a timely manner.

Training and advice
Provide comprehensive training recommendations and security policy optimization solutions to enterprises based on the drill results.






