Customer Benefits

Solution Background
With the rapid development and application of technologies such as big data, industrial internet, cloud computing, and artificial intelligence, on the one hand, these new technologies have accelerated the process of enterprises' digital business and brought about the prosperity of the digital economy; on the other hand, these new technologies have also made software architectures increasingly complex and new attack methods emerge, resulting in more security vulnerabilities being exposed in enterprise business systems. Against the backdrop of frequent cybersecurity incidents, enterprises' awareness of cybersecurity risks has been continuously strengthened, and vulnerability management has been increasingly valued by more and more enterprises and has become an important part of their cybersecurity strategies.
Requirement Analysis
Solution Introduction
The Vulnerability Management solution is designed to help organizations systematically identify, assess, remediate, and prevent security vulnerabilities in their information systems, thereby reducing the risk of cyberattacks and protecting sensitive data. By integrating advanced technologies and processes, the solution provides a comprehensive framework to ensure information security while meeting regulatory compliance requirements.
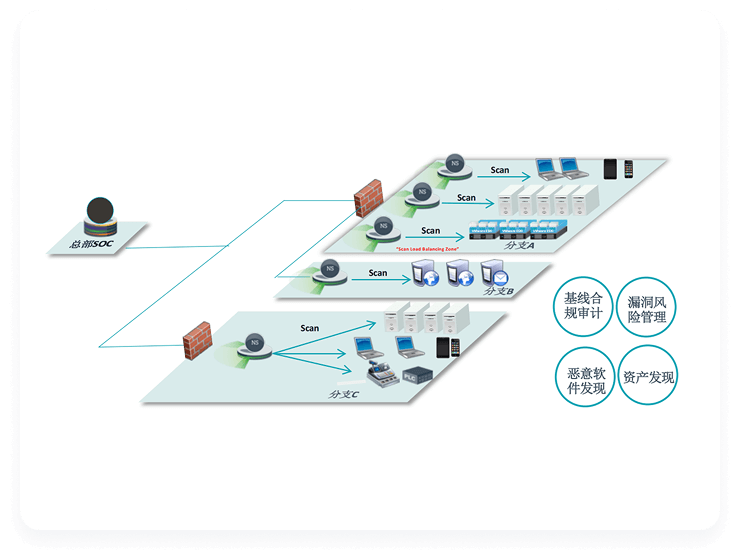
Solution Advantages

Wide asesst coverage
Supports scanning of various mainstream information systems such as operating systems, databases, middleware, network equipment, security equipment, and commonly used software.

Comprehensive baseline check
Automatically identify and analyze security configuration issues of various types of devices and systems, avoiding the potential risks of errors caused by traditional manual inspection methods.

Vulnerability Prioritization Technology (VPT)
Based on threat intelligence and real-time vulnerability exploitation situations, threat scores are assigned to vulnerabilities. By fixing 5% of the vulnerabilities, the security level can be enhanced by 90%.

Distributed deployment
Flexible deployment, powerful performance, effectively solving the problem of complex customer environments where vulnerabilities cannot be centrally managed.





