Customer Benefits

Solution Background
With the acceleration of global economic integration, the business scope of enterprises continues to expand, and cross-border and cross-regional operations have led to an exponential increase in the complexity of compliance management. Enterprises urgently need professional security and compliance consulting services to ensure that they can move forward steadily in a complex regulatory environment and achieve sustainable development.
Requirement Analysis
Solution Introduction
The members of the service team hold authoritative certificates such as CISSP and CISA, and have rich practical experience. They carry out their work in accordance with the industry-leading consulting methodologies. Based on the assessment results, combined with the industry characteristics and business actual needs of the enterprise, they customize information security strategies and management systems, including but not limited to the design of security organizational structure, the formulation of security management systems, and the planning of security technical architectures, etc. This enables the enterprise to always maintain a leading position on the path of security compliance and calmly cope with various internal and external challenges.
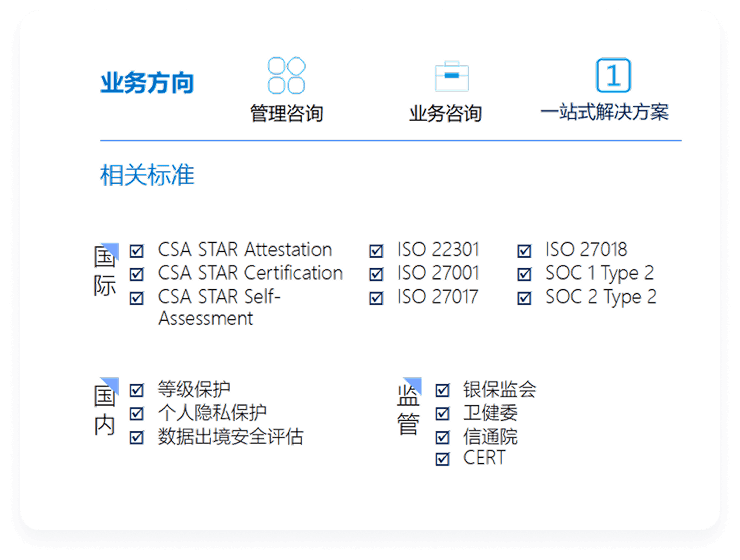
Solution Advantages

Service customization
We delve into the core of the enterprise and tailor exclusive solutions that are practical and effective.

Comprehensive coverage
Covering the entire life cycle of security compliance, it provides one-stop problem resolution and reduces the cost and risk of coordinating with multiple suppliers.

Targeted for implementation
Experts are well versed in technology and regulations, and deeply integrate them into solution design and implementation to avoid the risk of disconnection between technology and regulations.

Continuous innovation
Keep up with industry development, introduce cutting-edge elements, and provide customers with leading services.






