Customer Benefits

Solution Background
In today’s complex and dynamic cybersecurity landscape, assessing security effectiveness is essential for protecting information assets. As cyber threats grow more sophisticated, enterprise defenses face unprecedented pressure. While organizations invest heavily in layered protections—such as firewalls, intrusion detection systems, and antivirus solutions—the real-world effectiveness of these controls remains hard to measure. At the same time, stricter cybersecurity regulations require not only implementation but also demonstrable proof of security efficacy to meet compliance and build stakeholder trust. In this context, security effectiveness verification services offer a precise and comprehensive way to evaluate defenses, enabling organizations to understand their security posture and respond confidently to evolving threats.
Requirement Analysis
Solution Introduction
This service leverages a mature BAS platform and adheres to standard attack simulation methodologies, conducting customized simulated attacks tailored to the enterprise's network architecture, business processes, and security policies. Based on the simulated attack results, a detailed security assessment report is provided to the enterprise, identifying weaknesses and vulnerabilities in security defenses and providing targeted improvement recommendations and optimization solutions.
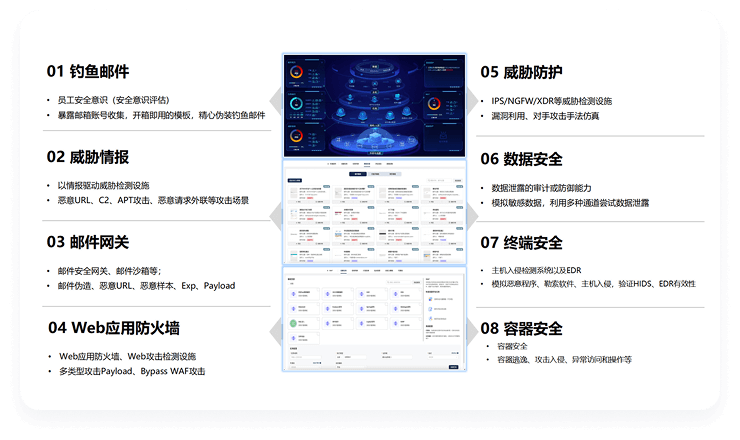
Solution Advantages

Defend against threats faster
・Dynamic and automated
・High-frequency, regular verification
・Full coverage, no blind spots
・Connect with security operation system
・High-frequency, regular verification
・Full coverage, no blind spots
・Connect with security operation system

Eliminate defensive blind spots
・Systematic security verification
・Changes in network and security policies
・Employee resignation and recruitment
・Invisible defensive gaps
・Changes in network and security policies
・Employee resignation and recruitment
・Invisible defensive gaps

Fit the attacking tactics
・Advanced, covert attack techniques
・Newly-exploited vulnerabilities
・Anti-virus exemption, bypassing technology
・IoC, attack adversary TTPs
・Newly-exploited vulnerabilities
・Anti-virus exemption, bypassing technology
・IoC, attack adversary TTPs

Continuous innovation
・Keep pace with industry development, introduce cutting-edge elements, and provide customers with leading services.






