Customer Benefits

Solution Background
The limitations of the traditional endpoint management approach lie in its inability to comprehensively cover endpoint types and network environments, and its inability to achieve unified management, resulting in the construction of isolated security systems. This not only leads to low management efficiency but also poses risks of security gaps between different security systems. The technology-oriented solutions only provide technical means and do not focus on management outcomes, making it difficult to achieve the expected management effects. Endpoint devices will accumulate an increasing number of client applications. In most cases, a single endpoint may have as many as five or more security agents installed. This not only makes the endpoint operation slower and the user experience worse, but also forces enterprise security personnel to be trapped in a large amount of operational work for the products.
Requirement Analysis
Solution Introduction
Building human-centric endpoint security
Security professionals must build a comprehensive, effective defense architecture that meets the evolving needs of cybersecurity, rather than simply piling up products as in the past. Improving security capabilities without sacrificing user experience is crucial. During the planning and development phases of information systems, security factors should be integrated, keeping in mind that human error is the primary cause of security vulnerabilities, to mitigate potential risks arising from inherent system security issues.
Security professionals must build a comprehensive, effective defense architecture that meets the evolving needs of cybersecurity, rather than simply piling up products as in the past. Improving security capabilities without sacrificing user experience is crucial. During the planning and development phases of information systems, security factors should be integrated, keeping in mind that human error is the primary cause of security vulnerabilities, to mitigate potential risks arising from inherent system security issues.
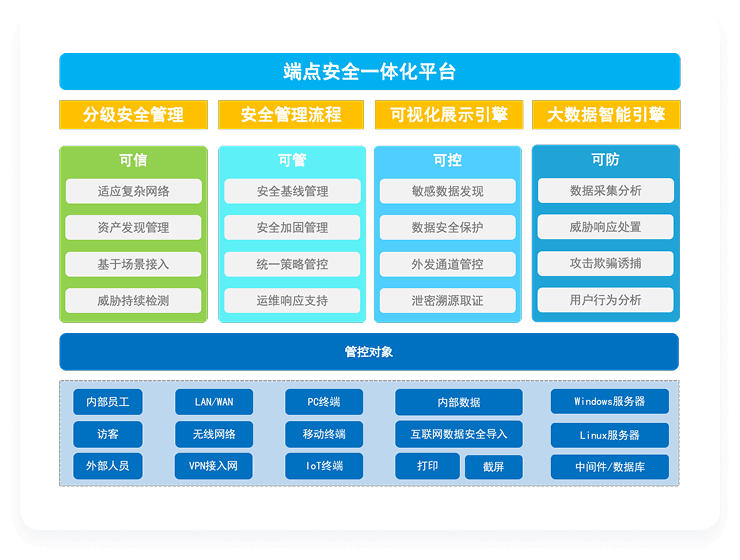
Solution Advantages

Trusted
Implement access control based on mandatory policies to ensure that the accessing endpoints are "trusted"

Manageable
Strengthen the security protection capabilities at the endpoints, enhance the immunity, and ensure that the endpoints are "manageable"

Defensible
Combining endpoint pro-active defense, threat detection and automatic response are achieved, enabling the endpoint to be "defensible"

Controllable
Take full-life cycle data management control measures to ensure data is "controllable"






