Customer Benefits

Solution Background
With the acceleration of enterprise digital transformation, business systems have been continuously expanded, covering multiple fields such as cloud computing, mobile applications, and the Internet of Things. This has led to a significant increase in the attack surface of enterprises. Security penetration testing, as an active security assessment method, can help enterprises identify and fix potential security vulnerabilities in advance, enhance the overall security defense capabilities, and ensure the stability and sustainable development of the business.
Requirement Analysis
Solution Introduction
Penetration testing is a type of security testing that requires both high levels of confrontation and customization. After obtaining written authorization, security engineers attempt to simulate the vulnerability discovery techniques and attack methods that hackers might use as comprehensively as possible (compared to hacker attacks, the results are predictable). They conduct in-depth probing of the security of the target network, hosts, databases, and application systems to identify the weak points in the system.
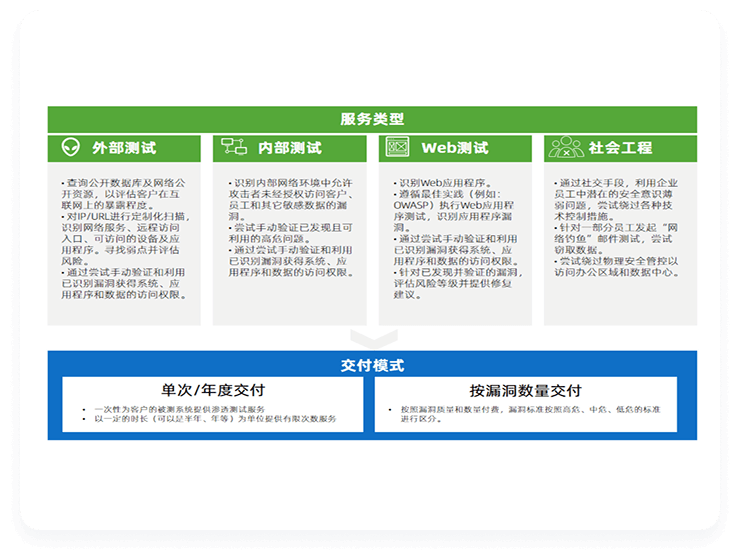
Solution Advantages

Multi-dimensional comprehensive testing
Comprehensive penetration testing from multiple dimensions, including external networks, internal networks, mobile applications, and web applications, can comprehensively and systematically evaluate the security of enterprise information systems and provide enterprises with complete security assessment results.

Deep vulnerability mining
By combining advanced technical tools with manual testing, we can deeply explore logical vulnerabilities and security risks in specific business scenarios, providing enterprises with more valuable security vulnerability information.

Professional team and authoritative certification
The security team brings together many top security experts in the industry, who are able to accurately respond to various complex network security challenges and provide enterprises with high-quality and reliable security operation services.

Customized service solutions
We gain an in-depth understanding of the company's unique business model, network architecture, and security needs to ensure that the service plan is closely aligned with the company's actual situation, maximize the benefits of the service, and meet the company's security operation needs at different stages of development.






