Customer Benefits
Solution Background
Enterprises have a large user base with diverse behaviors, including daily employee operations, remote access by partners, and customer interactions with enterprise systems. These behaviors generate massive amounts of data, but enterprises lack effective means to conduct in-depth analysis of this data to uncover hidden abnormal behavior patterns and potential security risks. User and entity behavior analysis technology can help enterprises extract valuable information from this complex user and entity behavior data, promptly identify and prevent security threats, and ensure the security of enterprise information assets and the stable operation of their businesses.
Requirement Analysis
Solution Introduction
Through aggregated analysis of security information and events, we predict, monitor, analyze, trace, and conduct digital forensics on violations, business fraud, data leaks, commercial espionage, and other potential behaviors that could undermine the security and continuity of a company's core business operations by employees and business stakeholders (upstream and downstream). Data analysis results are used as a basis for business decision-making in HR, internal audit, and compliance departments. Services include:
- Establishing a behavioral baseline
- Abnormal behavior detection
- Risk Score
- Advanced Threat Detection
- Real-time correlation analysis
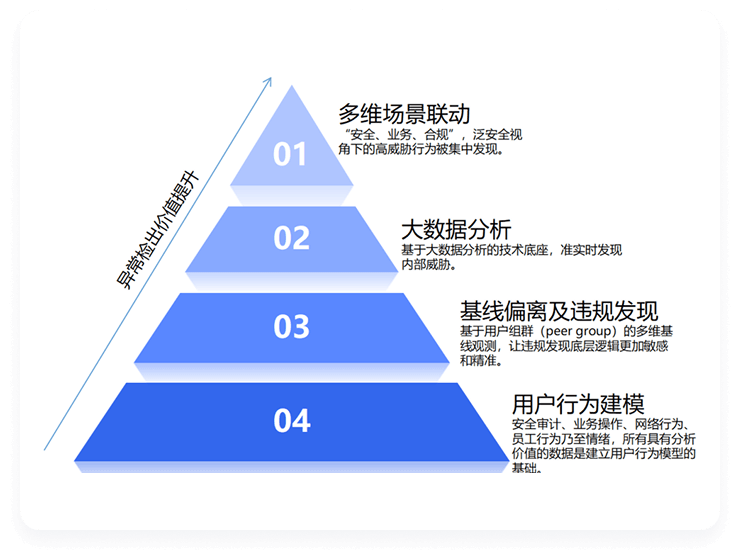
Solution Advantages

In-depth industry experience
Customized behavioral analysis models can be provided for specific industries.

Comprehensive coverage
Covering the entire life cycle of security compliance, it provides one-stop problem resolution and reduces the cost and risk of coordinating with multiple suppliers.

Implementation
Experts are well versed in technology and regulations, and deeply integrate them into solution design and implementation to avoid the risk of disconnection between technology and regulations.

Continuous innovation
Keep up with industry development, introduce cutting-edge elements, and provide customers with leading services.






